CompTIA Pentest+ (PT0-002) Complete Penetration Testing Guide
16
March
2025
9.76 GB | 34min 34s | mp4 | 1280X720 | 16:9
Genre:eLearning |Language:English
Files Included :
1 -Introduction.mp4 (98.85 MB)
2 -How to access the CompTIA Pentest+ lab.mp4 (16.95 MB)
1 -What is network attacks.mp4 (29.48 MB)
10 -What mac spoofing attack LAB in Linux.mp4 (106.69 MB)
11 -VLAN hopping and double Tagging attack.mp4 (100.09 MB)
12 -DNS poisoning Attack using ettercap.mp4 (149.56 MB)
13 -Password Attacks.mp4 (64.09 MB)
14 -Password attack Demonstration LAB.mp4 (93.06 MB)
15 -Pass the hash Attack and Kerboroasting Attack.mp4 (42.56 MB)
16 -Kerboroasting a Complete LAB demo.mp4 (210.38 MB)
17 -On path attack in Network.mp4 (72.63 MB)
18 -LLMNR and NBT-NS Poisoning Attack with Example and LAB.mp4 (81.49 MB)
19 -Advance password attacks and prevention techniques.mp4 (34.92 MB)
2 -Load balance or stress testing.mp4 (63.43 MB)
20 -NAC Bypass Attack in Network.mp4 (27.42 MB)
21 -Using Reverse and bind Shell LAB.mp4 (101.85 MB)
22 -Exploit Resources Exploit-DB or Chaining.mp4 (137.29 MB)
3 -Protect transmission stream.mp4 (79.49 MB)
4 -Bluetooth Attacks in Network.mp4 (52.5 MB)
5 -RFID and NFC Attacks.mp4 (47.25 MB)
6 -ARP poisoning Attack.mp4 (67.62 MB)
7 -ARP poisoning attack using ettercap to capture password.mp4 (55.51 MB)
8 -Arp Spoofing Attack with arpspoof tool.mp4 (53.21 MB)
9 -MAC table overflow Attack.mp4 (26.48 MB)
1 -Securing Wireless Communication.mp4 (103.74 MB)
10 -Evil Twins attack.mp4 (38.55 MB)
2 -Signal transmission and Exploitation.mp4 (59.3 MB)
3 -Quick demo on capture wireless data.mp4 (32.62 MB)
4 -deauthentication attack inside wireless network.mp4 (31.08 MB)
5 -LAB deauthentication attack agains wireless network.mp4 (66.16 MB)
6 -Wi-Fi Jamming Attack.mp4 (28.05 MB)
7 -Crack WPA and WPA2 key with Demo.mp4 (59.01 MB)
8 -Cracking WEP - LAB.mp4 (33.45 MB)
9 -Cracking WPS wireless security.mp4 (54.25 MB)
1 -Mobile device vulnerability and deployment methods.mp4 (70.19 MB)
2 -Controlling access.mp4 (54.52 MB)
3 -EMM Security policies and protecting data.mp4 (94.1 MB)
4 -Vulnerability and protection of Android and iOS device.mp4 (84.48 MB)
5 -Attacking on mobile platforms.mp4 (70.11 MB)
6 -Moving through attacks and spyware.mp4 (25.89 MB)
7 -Bluetooth attack and malware analysis.mp4 (45.62 MB)
1 -Identify Vulnerabilities and attacks on IoT Devices.mp4 (184.05 MB)
2 -Leveraging the Protocols.mp4 (55.69 MB)
3 -LAB Discovering IoT devices with Shodan.mp4 (58.66 MB)
4 -Recognize Other Vulnerable Systems.mp4 (156.16 MB)
1 -Exposing Sensitive Data with improper error handling.mp4 (66.49 MB)
10 -Executing Cross Site Scripting XSS attack and Web proxy.mp4 (36.77 MB)
11 -LAB SQL Injection Attack.mp4 (33.1 MB)
12 -Overview of Web Testing Tools.mp4 (24.54 MB)
13 -Exploring the Browser Exploit Framework BeEF.mp4 (32.59 MB)
2 -Missing Input Validation and Signing the Code.mp4 (46.75 MB)
3 -Causing a Race condition.mp4 (39.92 MB)
4 -Hijacking Session Credentials.mp4 (74.96 MB)
5 -Crafting Request Forgery Attacks.mp4 (59.82 MB)
6 -Privilege Escalation.mp4 (45.31 MB)
7 -Upgrading a Non-Interactive Shell.mp4 (41.75 MB)
8 -Identifying SQLi Vulnerabilities.mp4 (77.2 MB)
9 -Traversing Files Using Invalid Input.mp4 (43.6 MB)
1 -Objectives Perform System Hacking.mp4 (10.85 MB)
2 -Net framework and Powershell in Windows 10.mp4 (37.06 MB)
3 -Command and Control C2 Frameworks.mp4 (42.16 MB)
4 -LAB Using Reverse Shell and Bind Shell.mp4 (52.85 MB)
5 -Remote Access Tool - Netcat.mp4 (43.32 MB)
6 -Communicating withing a Secure Shell (SSH).mp4 (66.03 MB)
7 -Analyze Exploit code.mp4 (64.49 MB)
1 -Analyzing and automating tasks using scripting.mp4 (97.12 MB)
2 -Basic understanding about scripting languages.mp4 (97.68 MB)
3 -LAB Exploring Programming Shells.mp4 (118.32 MB)
4 -Basics of logic construct.mp4 (94.15 MB)
5 -Data structure in python.mp4 (65.47 MB)
6 -LAB Automate the penetration testing process.mp4 (31.87 MB)
7 -Automate Penetration Testing.mp4 (29.22 MB)
1 -Password cracking method online and offline.mp4 (76.67 MB)
2 -Dictionary attack and bypass lockout policy.mp4 (71.42 MB)
3 -Bruteforce and password spraying attack.mp4 (31.39 MB)
4 -Test Credential as Linux and Windows.mp4 (69.98 MB)
5 -LAB password attack.mp4 (92.27 MB)
6 -LAB post exploitation Techniques.mp4 (289.7 MB)
1 -Define and outlining the communication Path.mp4 (57.48 MB)
2 -Communicating with Client Counterparts.mp4 (16.54 MB)
3 -Defining Contacts.mp4 (33.88 MB)
4 -Triggering Communication Events and Prioritize findings.mp4 (43.07 MB)
5 -Providing Situational Awareness and Criminal Activity.mp4 (45.68 MB)
6 -Triggering and Investigating False Positives.mp4 (36.14 MB)
7 -Presenting the Findings.mp4 (44.67 MB)
8 -Sharing and Building Reports with Dardis and Nessus.mp4 (26.24 MB)
1 -Identify Report Audience.mp4 (68.2 MB)
2 -List Report Contents.mp4 (317.99 MB)
3 -Define Best Practices for Reports.mp4 (193.65 MB)
1 -Cyber Health and Risk management.mp4 (91.24 MB)
2 -Penetration Testing Processes.mp4 (84.51 MB)
3 -PCI DSS Payment Card Industry Data security standard.mp4 (92.26 MB)
4 -GDPR and other laws.mp4 (79.26 MB)
5 -Identifying Pentesting Frameworks.mp4 (47.86 MB)
6 -Different penetration testing frameworks.mp4 (56.03 MB)
7 -Investigating CVE and CWE.mp4 (69.53 MB)
1 -Hardening the System.mp4 (67.01 MB)
2 -Sanitizing User Input.mp4 (61.08 MB)
3 -Implementing Multifactor Authentication MFA.mp4 (58.89 MB)
4 -Encrypting the password.mp4 (38.33 MB)
5 -Process-Level Remediation and Patch Management.mp4 (65.13 MB)
6 -Key rotation and Certificate Management.mp4 (49.05 MB)
7 -Providing Secret Management Solution and Network Segmentation.mp4 (38.18 MB)
1 -Assess Environmental Considerations.mp4 (161.76 MB)
2 -Outline the Rules of Engagement.mp4 (93.52 MB)
3 -Prepare Legal Documents.mp4 (99.29 MB)
1 -Discover the Target.mp4 (103.18 MB)
2 -Gather information from source code repository.mp4 (47.65 MB)
3 -Google hacking and Google hacking database.mp4 (59.8 MB)
4 -Gather information from archive and image search.mp4 (56.65 MB)
5 -Retrieve Website information.mp4 (86.76 MB)
6 -Testing ssl and TLS certificate.mp4 (89.36 MB)
7 -LAB nslookup dig and whois -1.mp4 (44.55 MB)
8 -Discover Open-Source Intelligence Tools.mp4 (103.7 MB)
9 -LAB Use tool harvester for gathering emails.mp4 (27.12 MB)
1 -Social engineering motivation Techniques.mp4 (131.05 MB)
2 -Social engineering attack.mp4 (99.09 MB)
3 -Social engineering Countermeasures.mp4 (30.02 MB)
4 -Some other type of social engineering attacks.mp4 (61.69 MB)
5 -Physical attacks in the term of social engineering.mp4 (125.31 MB)
6 -LAB - Social Engineering Toolkit.mp4 (103.83 MB)
1 -Overview of Vulnerability.mp4 (42.72 MB)
2 -Life Cycle of Vulnerability.mp4 (43.3 MB)
3 -Researching Vulnerabilities - CVE.mp4 (74.49 MB)
4 -CWE - Common Weakness Enumeration.mp4 (59.79 MB)
5 -CAPEC- Common Attack Pattern Enumeration and Classification.mp4 (64.54 MB)
6 -MITRE Attack Adversarial Tactics, Techniques and Common Knowledge.mp4 (97.25 MB)
1 -Web vulnerability scanning with Nikto.mp4 (31.89 MB)
2 -Web Vulnerability Scanning with Wapiti.mp4 (25.65 MB)
3 -Vulnerability scanning with OpenVAS.mp4 (47.09 MB)
4 -OpenVAS Report Analyze.mp4 (23.77 MB)
5 -Automating Vulnerability Scanning with Nessus.mp4 (57.31 MB)
6 -Nessus Scan Analyze the scan Report.mp4 (27.08 MB)
1 -nmap basic syntax for host discovery in the netowrk.mp4 (54.07 MB)
2 -Different scanning Techniques to Bypass Firewall, IDS and IPS.mp4 (44.95 MB)
3 -LAB host discovery by using nmap.mp4 (60.47 MB)
4 -Different techniques used for scanning ports.mp4 (63.18 MB)
5 -Fingerprinting and Enumeration with nmap.mp4 (88.66 MB)
6 -nmap script engine for Vulnerability scanning.mp4 (69.22 MB)
1 -Flying under the Radar.mp4 (93.9 MB)
2 -Bypassing network Access Control NAC.mp4 (19.74 MB)
3 -LOITL and covering the Track.mp4 (34.63 MB)
4 -Tiding Logs and Entries.mp4 (71.51 MB)
5 -Using Steganography to Hide and Conceal Data.mp4 (59.26 MB)
6 -Data Exfiltration and SSH Channel.mp4 (48 MB)
7 -Netcat and winrm to manage covert channel.mp4 (37.67 MB)
8 -Using Proxy and Proxy Chaining.mp4 (23.58 MB)]
Screenshot
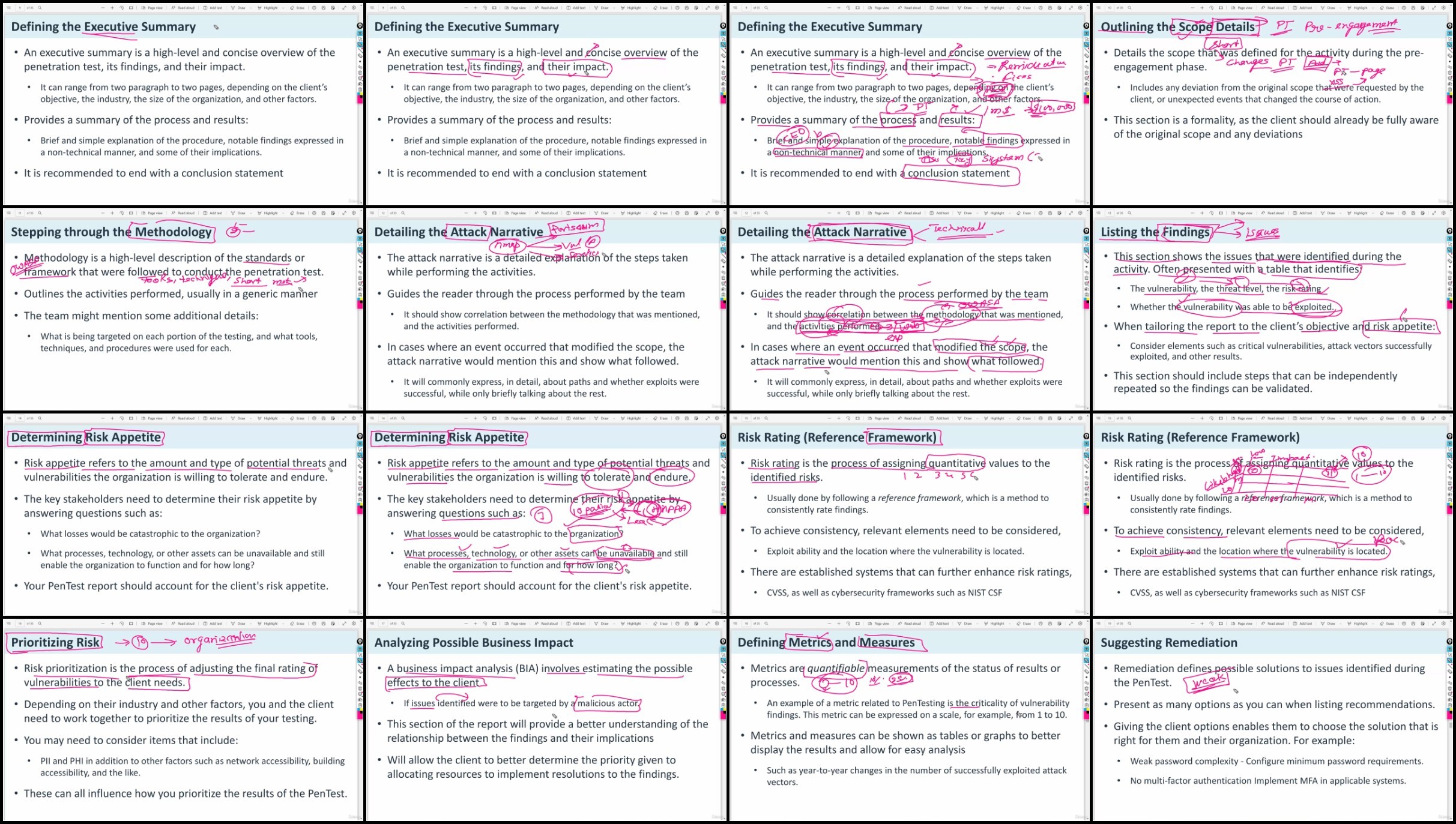
TurboBit
https://turbobit.net/ncb2nquli8jl.html
https://turbobit.net/b7r9a5zxjce6.html
https://turbobit.net/6qc978rlvuxr.html
https://turbobit.net/8qbxt7t8rpbs.html
https://turbobit.net/x6lhbayc42cs.html
https://turbobit.net/322luwjch7vn.html
https://turbobit.net/b3q7gzanov16.html
https://turbobit.net/oczsj8d2pbii.html
https://turbobit.net/4hysibey8p6r.html
https://turbobit.net/b5aof7u79o1v.html
RapidGator
https://rapidgator.net/file/2e70d55c4dcf4ff8c5af4dc24da443f4/
https://rapidgator.net/file/4dbdc46492c2dd0fbf57be895edda63d/
https://rapidgator.net/file/b7c46741531a12aa915925437c88000e/
https://rapidgator.net/file/c0b745529dc6147ae5f74d9a92833f9f/
https://rapidgator.net/file/7014ac23d99ae7a0689379e57e556ae3/
https://rapidgator.net/file/608353cf9ee352471066269b886b50ec/
https://rapidgator.net/file/d4b81565661bf238031897a45f8b2b44/
https://rapidgator.net/file/b885a6fccc8405f79d08d16886e93690/
https://rapidgator.net/file/3e2e8b7b7f01e9dc1864b76971e44f32/
https://rapidgator.net/file/09faf2d33c2ed4a9d474adf6b10f1f7b/
Note:
Only Registed user can add comment, view hidden links and more, please register now
Only Registed user can add comment, view hidden links and more, please register now
Related Posts

